How to 100% pass 70-417 exam? GreatExam offers you all the 70-417 exam questions and answers which are the same as your real test with 100% correct and coverage rate. Our 70-417 practice test is unparalleled in quality and is 100% guaranteed to make you pass 70-417 exam. All the 70-417 prepare material are the latest. Here are some free share of Microsoft 70-417 dumps.
QUESTION 341
You have a virtual machine named VM1 that runs on a host named Host1.
You configure VM1 to replicate to another host named Host2. Host2 is located in the same physical location as Host1.
You need to add an additional replica of VM1.
The replica will be located in a different physical site.
What should you do?
A. From VM1 on Host2, click Extend Replication.
B. On Host1, configure the Hyper-V settings.
C. From VM1 on Host1, click Extend Replication.
D. On Host2, configure the Hyper-V settings.
Answer: A
Explanation:
http://blogs.technet.com/b/virtualization/archive/2013/12/10/hyper-v-replica-extend-replication.aspx
Once that is done, go to replica site and from Hyper-V UI manager select the VM for which you want to extend the replication. Right click on VM and select “Replication->Extend Replication …”. This will open Extend Replication Wizard which is similar to Enable Replication Wizard.
http://technet.microsoft.com/en-us/library/dn551365.aspx
http://technet.microsoft.com/en-us/library/jj134240.aspx
NOTE: You configure a server to receive replication with Hyper-V Manager, in this situation the replica site is assumed to be the Replica Server. Therefore you extend replication from VM1 on Host2.
QUESTION 342
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named File1 that runs a Server Core Installation of Windows Server 2012 R2.
File1 has a volume named D that contains home folders. File1 creates a shadow copy of volume D twice a day.
You discover that volume D is almost full.
You add a new volume named H to File1.
You need to ensure that the shadow copies of volume D are stored on volume H.
Which command should you run?
A. The Set-Volume cmdlet with the -driveletter parameter
B. The vssadmin.exe create shadow command
C. The Set-Volume cmdlet with the -path parameter
D. The vssadmin.exe add shadowstorage command
Answer: D
Explanation:
A. Sets or changes the file system label of an existing volume. -DriveLetter Specifies a letter used to identify a drive or volume in the system.
B. Displays current volume shadow copy backups and all installed shadow copy writers and providers. Shadow Creates a new shadow copy of a specified volume.
C. Sets or changes the file system label of an existing volume -Path Contains valid path information.
D. Displays current volume shadow copy backups and all installed shadow copy writers and providers.
AddShadowStroage Adds a shadow copy storage association for a specified volume.
http://technet.microsoft.com/en-us/library/cc754968(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/hh848673(v=wps.620).aspx
QUESTION 343
Your network contains an Active Directory domain named contoso.com.
The domain contains six domain controllers.
The domain controllers are configured as shown in the following table.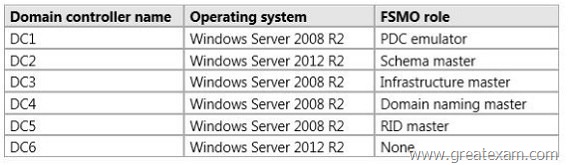
The network contains a server named Server1 that has the Hyper-V server role installed.
DC6 is a virtual machine that is hosted on Server1.
You need to ensure that you can clone DC6.
Which FSMO role should you transfer to DC2?
A. Rid master
B. Domain naming master
C. PDC emulator
D. Infrastructure master
Answer: C
Explanation:
The clone domain controller uses the security context of the source domain controller (the domain controller whose copy it represents) to contact the Windows Server 2012 R2 Primary Domain Controller (PDC) emulator operations master role holder (also known as flexible single master operations, or FSMO).
The PDC emulator must be running Windows Server 2012 R2, but it does not have to be running on a hypervisor.
http://technet.microsoft.com/en-us/library/hh831734.aspx
QUESTION 344
Drag and Drop Question
Your network contains an Active Directory domain named adatum.com. The domain contains three servers. The servers are configured as shown in the following table.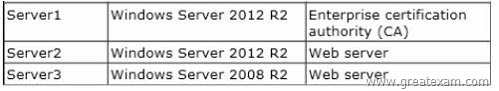
Server1 is configured as shown in the exhibit. (Click the Exhibit button.)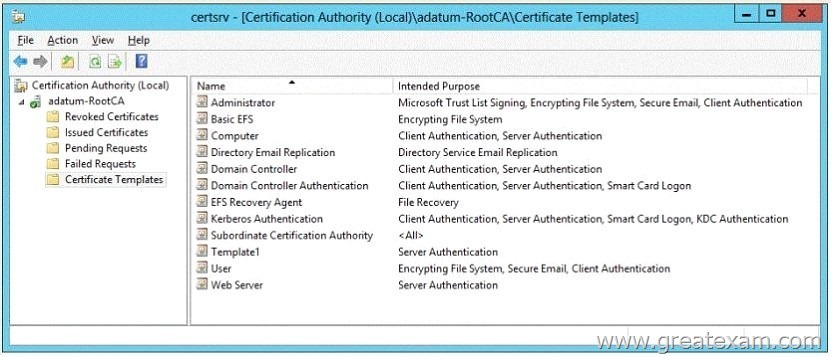
Template1 contains custom cryptography settings that are required by the corporate security team.
On Server2, an administrator successfully installs a certificate based on Template1.
The administrator reports that Template1 is not listed in the Certificate Enrollment wizard on Server3, even after selecting the Show all templates check box.
You need to ensure that you can install a server authentication certificate on Server3.
The certificate must comply with the cryptography requirements.
Which three actions should you perform in sequence? To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.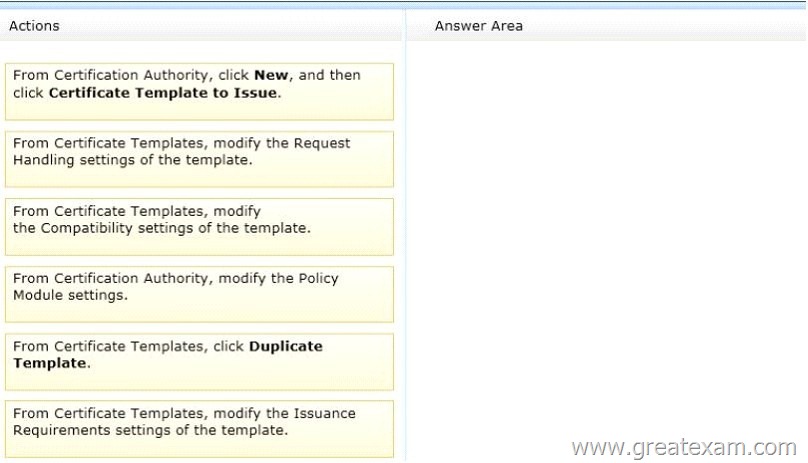
Answer: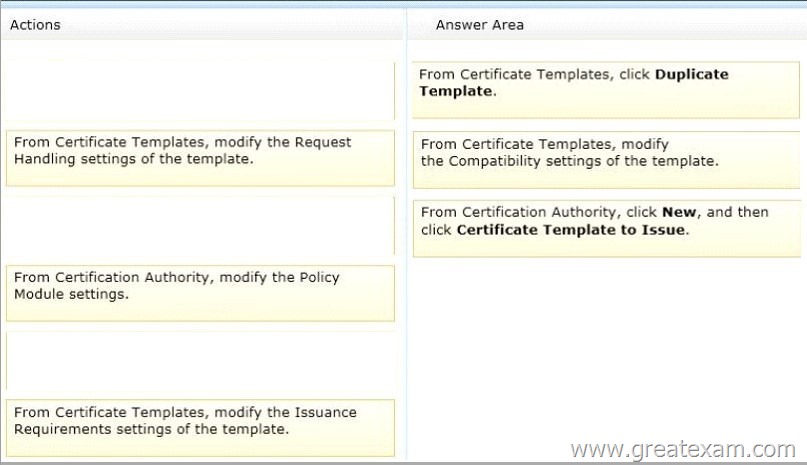
Explanation:
http://social.technet.microsoft.com/wiki/contents/articles/15897.certificate-templates-not-available-for-windows-7-and-windows-server-2008-r2-certificate-recipients-using-certificate-enrollment-web-services.aspx
QUESTION 345
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the DNS Server server role installed.
Server1 has a zone named contoso.com.
The zone is configured as shown in the exhibit. (Click the Exhibit button.)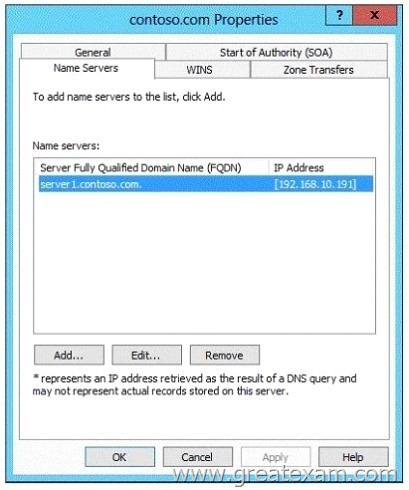
You need to assign a user named User1 permission to add and delete records from the contoso.com zone only.
What should you do first?
A. Enable the Advanced view from DNS Manager.
B. Add User1 to the DnsUpdateProxy group.
C. Run the New Delegation Wizard.
D. Configure the zone to be Active Directory-integrated.
Answer: C
Explanation:
– DNS namespace Parent -> DNS namespace child : delegation
– DNS namespace child -> DNS namespace Parent : nothing to do with contiguous DNS namespace (or conditional forwarder for non-contiguous DNS namespace)
QUESTION 346
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server3 that runs Windows Server 2012 R2 and has the DHCP Server server role installed.
DHCP is configured as shown in the exhibit. (Click the Exhibit button.)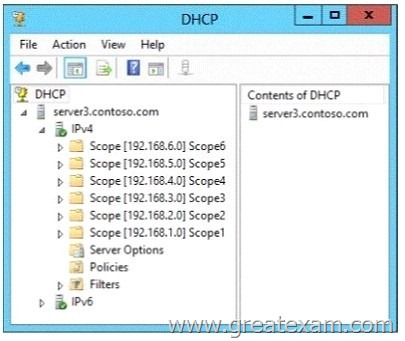
You need to ensure that only Scope1, Scope3, and Scope5 assign the same DNS servers to DHCP clients. The solution must minimize administrative effort.
What should you do?
A. Create a superscope and a filter.
B. Create a superscope and scope-level policies.
C. Configure the Server Options.
D. Configure the Scope Options.
Answer: D
Explanation:
Any DHCP scope options configured for assignment to DHCP clients
http://technet.microsoft.com/en-us/library/dd759218.aspx
http://technet.microsoft.com/en-us/library/cc757682(v=WS.10).aspx
QUESTION 347
Hotspot Question
Your network contains an Active Directory domain named contoso.com.
You have a Dynamic Access Control policy named Policy1.
You create a new Central Access Rule named Rule1.
You need to add Rule1 to Policy1.
What command should you run? To answer, select the appropriate options in the answer area.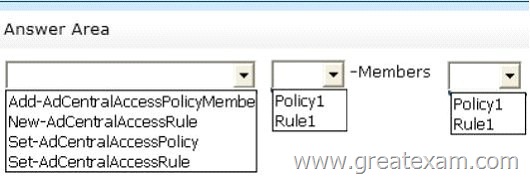
Answer: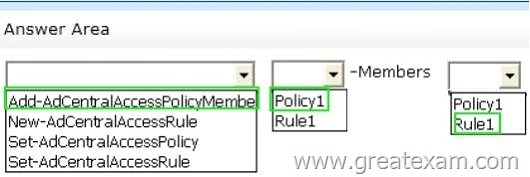
QUESTION 348
Your network contains an Active Directory domain named contoso.com. The domain contains domain controllers that run Windows Server 2008, Windows Server 2008 R2 Windows Server 2012, and Windows Server 2012 R2.
A domain controller named DC1 runs Windows Server 2012 R2. DC1 is backed up daily.
During routine maintenance, you delete a group named Group1.
You need to recover Group1 and identify the names of the users who were members of Group1 prior to its deletion.
You want to achieve this goal by using the minimum amount of administrative effort.
What should you do first?
A. Perform an authoritative restore of Group1.
B. Mount the most recent Active Directory backup.
C. Use the Recycle Bin to restore Group1.
D. Reactivate the tombstone of Group1.
Answer: A
Explanation:
The Active Directory Recycle Bin does not have the ability to track simple changes to objects. If the object itself is not deleted, no element is moved to the Recycle Bin for possible recovery in the future. In other words, there is no rollback capacity for changes to object properties, or, in other words, to the values of these properties. There is another approach you should be aware of. Tombstone reanimation (which has nothing to do with zombies) provides the only way to recover deleted objects without taking a DC offline, and it’s the only way to recover a deleted object’s identity information, such as its objectGUID and objectSid attributes. It neatly solves the problem of recreating a deleted user or group and having to fix up all the old access control list (ACL) references, which contain the objectSid of the deleted object.
Restores domain controllers to a specific point in time, and marks objects in Active Directory as being authoritative with respect to their replication partners.
QUESTION 349
Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2.
Server1 and Server2 have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1. Cluster1 has access to four physical disks. The disks are configured as shown in the following table.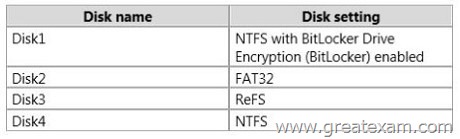
You need to ensure that all of the disks can be added to a Cluster Shared Volume (CSV).
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
A. Enable BitLocker on Disk4.
B. Disable BitLocker on Disk1.
C. Format Disk2 to use NTFS.
D. Format Disk3 to use NTFS.
Answer: CD
Explanation:
You cannot use a disk for a CSV that is formatted with FAT, FAT32, or Resilient File System (ReFS).
QUESTION 350
Hotspot Question
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. All domain controllers run Windows Server 2012 R2 and are configured as DNS servers. All DNS zones are Active Directory-integrated. Active Directory Recycle Bin is enabled.
You need to modify the amount of time deleted objects are retained in the Active Directory Recycle Bin.
Which naming context should you use? To answer, select the appropriate naming context in the answer area.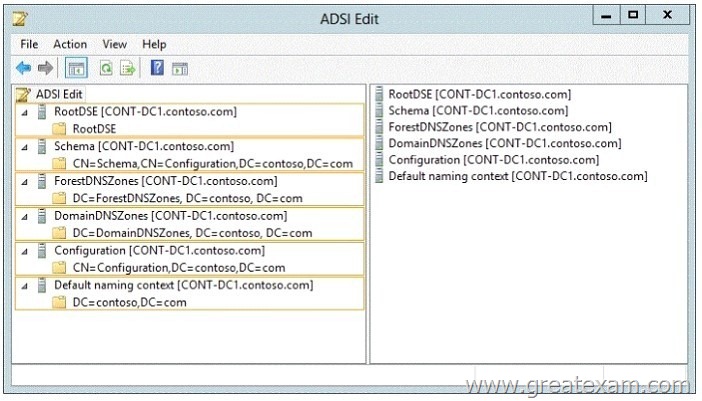
Answer: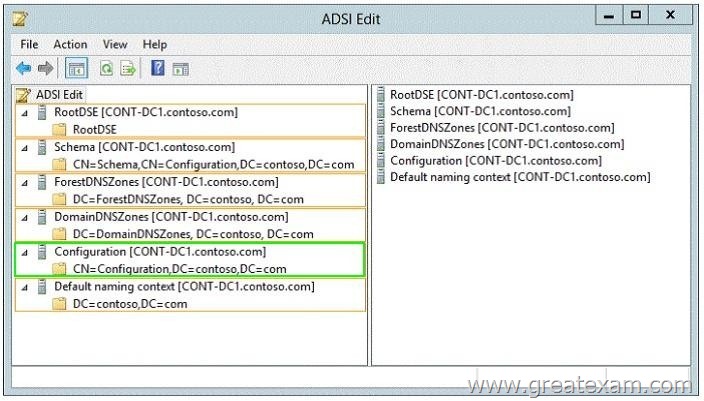
QUESTION 351
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. The domain contains a standalone server named Server2 that is located in a perimeter network. Both servers run the default installation of Windows Server 2012 R2.
You need to manage Server2 remotely from Server1.
What should you do?
A. From Server1, run the Enable-PsRemotingcmdlet.
B. From Server2, run the winrm command.
C. From Server2/ run the Enable-PsRemotingcmdlet.
D. From Server1, run the winrm command.
Answer: D
QUESTION 352
You have a server that runs Windows Server 2012 R2.
The disks on the server are configured as shown in the exhibit. (Click the Exhibit button.)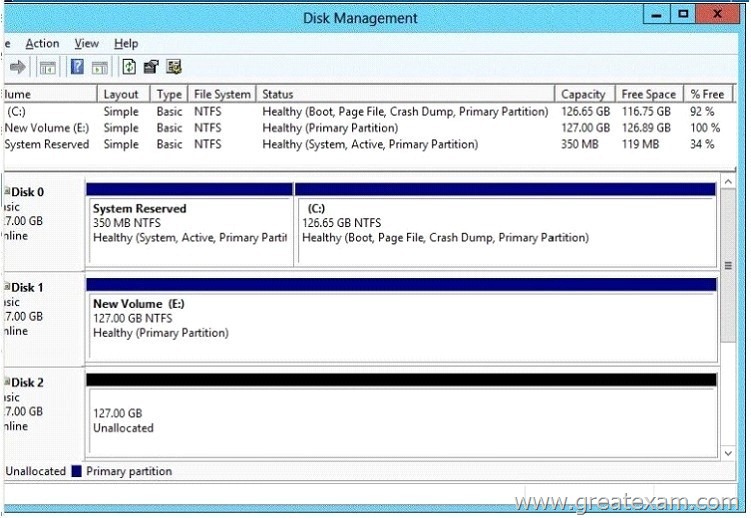
You need to create a storage pool that contains Disk 1 and Disk 2.
What should you do first?
A. Convert Disk 1 and Disk 2 to GPT disks
B. Create a volume on Disk 2
C. Convert Disk 1 and Disk 2 to dynamic disks
D. Delete volume E
Answer: D
Explanation:
Storage Pools use unallocated space thus you need to delete Volume E.
http://technet.microsoft.com/en-us/library/ff399688.aspx
QUESTION 353
Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that has the Network Policy Server server role installed. The domain contains a server named Server2 that is configured for RADIUS accounting.
Server1 is configured as a VPN server and is configured to forward authentication requests to Server2.
You need to ensure that only Server2 contains event information about authentication requests from connections to Server1.
Which two nodes should you configure from the Network Policy Server console? To answer, select the appropriate two nodes in the answer area.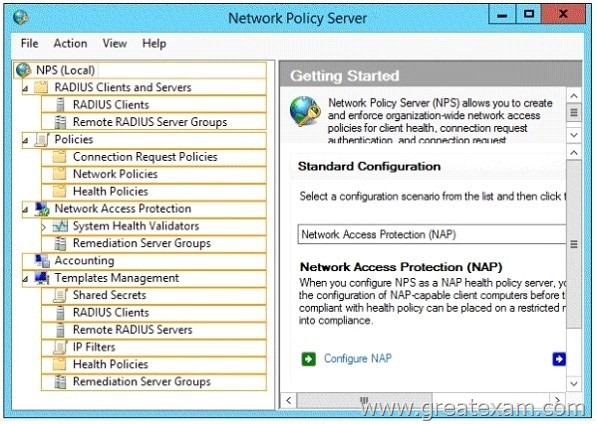
Answer: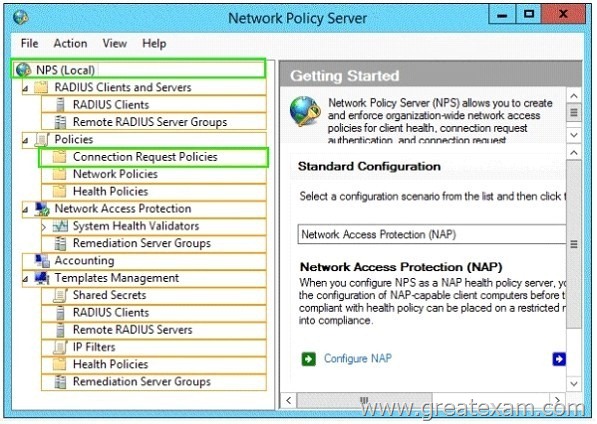
QUESTION 354
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. Server1 runs Windows Server 2012 R2 and has the Hyper-V server role installed.
On Server1, an administrator creates a virtual machine named VM1.
A user named User1 is the member of the local Administrators group on Server1.
User1 attempts to modify the settings of VM1 as shown in the following exhibit. (Click the Exhibit button.)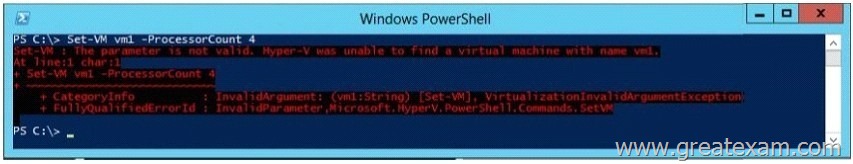
You need to ensure that User1 can modify the settings of VM1 by running the Set- Vmcmdlet.
What should you instruct User1 to do?
A. Run Windows PowerShell with elevated privileges.
B. Install the Integration Services on VM1.
C. Modify the membership of the local Hyper-V Administrators group.
D. Import the Hyper-V module.
Answer: A
Explanation:
You can only use the PowerShell snap-in to modify the VM settings with the vmcmdlets when you are an Administrator.
Thus best practices dictate that User1 run the Powershell with elevated privileges.
http://technet.microsoft.com/en-us/library/jj713439.aspx
QUESTION 355
Your network contains an Active Directory domain named contoso.com. The domain contains a member server named HVServer1. HVServer1 runs Windows Server 2012 R2 and has the Hyper-V server role installed.
HVServer1 hosts two virtual machines named Server1 and Server2.
Both virtual machines connect to a virtual switch named Switch1.
On Server2, you install a network monitoring application named App1.
You need to capture all of the inbound and outbound traffic to Server1 by using App1.
Which two commands should you run from Windows PowerShell? (Each correct answer presents part of the solution. Choose two.)
A. Get-VM “Server2” | Set-VMNetworkAdapter -IovWeight 1
B. Get-VM “Server1” | Set-VMNetworkAdapter -Allow/Teaming On
C. Get-VM “Server1” | Set-VMNetworkAdapter -PortMirroring Source
D. Get-VM “Server2” | Set-VMNetworkAdapter -PortMirroring Destination
E. Get-VM “Server1” | Set-VMNetworkAdapter -IovWeight 0
F. Get-VM “Server2” | Set-VMNetworkAdapter-AllowTeaming On
Answer: CD
Explanation:
* Get-VM will get the virtual machines from one or more Hyper-V hosts.
-ComputerName<String[]> is used to specify one or more Hyper-V hosts from which virtual machines are to be retrieved. NetBIOS names, IP addresses, and fully-qualified domain names are allowable. The default is the local computer — use “localhost” or a dot (“.”) to specify the local computer explicitly.
* Set-VMNetworkAdapter is used to configure features of the virtual network adapter in a virtual machine or the management operating system.
-PortMirroring<VMNetworkAdapterPortMirroringMode> is used to specify the port mirroring mode for the network adapter to be configured.
With Port Mirroring, traffic sent to or from a Hyper-V Virtual Switch port is copied and sent to a mirror port. There are a range of applications for port mirroring – an entire ecosystem of network visibility companies exist that have products designed to consume port mirror data for performance management, security analysis, and network diagnostics. With Hyper-V Virtual Switch port mirroring, you can select the switch ports that are monitored as well as the switch port that receives copies of all the traffic.
http://technet.microsoft.com/en-us/library/jj679878.aspx
QUESTION 356
Your network contains two Hyper-V hosts named Host1 and Host2. Host1 contains a virtual machine named VM1. Host2 contains a virtual machine named VM2. VM1 and VM2 run Windows Server 2012 R2.
You install the Network Load Balancing feature on VM1 and VM2.
You need to ensure that the virtual machines are configured to support Network Load Balancing (NLB).
Which virtual machine settings should you configure on VM1 and VM2?
A. DHCP guard
B. MAC address
C. Router guard
D. Port mirroring
Answer: B
Explanation:
When MAC addresses are not assigned to virtual machines, it could cause network problems.
http://blogs.msdn.com/b/clustering/archive/2010/07/01/10033544.aspx
QUESTION 357
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. Server1 has 8 GB of RAM.
Server1 hosts five virtual machines that run Windows Server 2012 R2.
The settings of a virtual machine named Server3 are configured as shown in the exhibit.
(Click the Exhibit button.)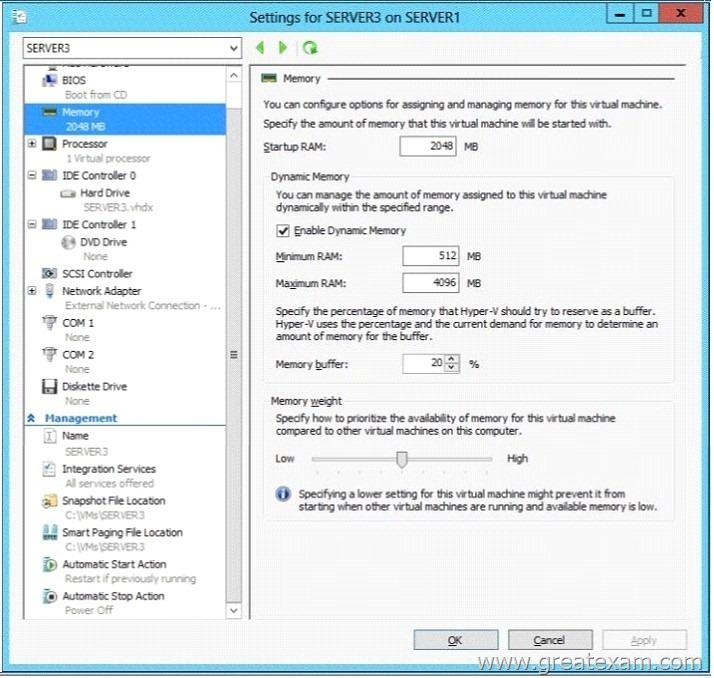
You need to ensure that when Server1 restarts, Server3 automatically resumes without intervention. The solution must prevent data loss.
Which settings should you modify?
A. BIOS
B. Automatic Stop Action
C. Automatic Start Action
D. Integration Services
Answer: B
Explanation:
The Automatic Stop Action setting should be modified because it will allow you to configure:
“Save the virtual machine state” option instructs Hyper-V Virtual Machine Management Service to save the virtual machine state on the local disk when the Hyper-V Server shuts down.
OR “Turn Off the virtual machine” is used by the Hyper-V Management Service (VMMS.exe) to gracefully turn off the virtual machine. OR “Shut down the guest operating system” is successful only if the “Hyper-V Shutdown” guest service is running in the virtual machine. The guest service is required to be running in the virtual machine as the Hyper-V VMMS.EXE process will trigger Windows Exit message which is received by the service. Once the message is received by the guest service, it takes the necessary actions to shut down the virtual machine.
http://www.altaro.com/hyper-v/hyper-v-automatic-start-and-stop-action/
QUESTION 358
Your network contains an Active Directory domain named contoso.com. The domain contains a member server named Server 1. Server1 runs Windows Server 2012 R2 and has the Hyper-V server role installed.
You create an external virtual switch named Switch1. Switch1 has the following configurations:
– Connection type: External network
– Single-root I/O virtualization (SR-IOV): Enabled
Ten virtual machines connect to Switch1.
You need to ensure that all of the virtual machines that connect to Switch1 are isolated from the external network and can connect to each other only. The solution must minimize network downtime for the virtual machines.
What should you do?
A. Remove Switch1 and recreate Switch1 as an internal network.
B. Change the Connection type of Switch1 to Private network.
C. Change the Connection type of Switch1 to Internal network.
D. Remove Switch1 and recreate Switch1 as a private network.
Answer: D
Explanation:
Original answer is B.
But the correct answer is D.
You cannot change the type of vswitch from external to private when SR-IOV is enabled at vswitch creation -> you need to recreate the vswitch.
QUESTION 359
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. The domain contains a virtual machine named VM1.
A developer wants to attach a debugger to VM1.
You need to ensure that the developer can connect to VM1 by using a named pipe.
Which virtual machine setting should you configure?
A. BIOS
B. Network Adapter
C. COM 1
D. Processor
Answer: C
Explanation:
Named pipes can be used to connect to a virtual machine by configuring COM 1.
http://support.microsoft.com/kb/819036
http://support.microsoft.com/kb/141709
QUESTION 360
You have a server named Server1 that runs Windows Server 2012 R2.
Server1 has three physical network adapters named NIC1, NIC2, and NIC3.
On Server1, you create a NIC team named Team1 by using NIC1 and NIC2. You configure Team1 to accept network traffic on VLAN 10.
You need to ensure that Server1 can accept network traffic on VLAN 10 and VLAN 11. The solution must ensure that the network traffic can be received on both VLANs if a network adapter fails.
What should you do?
A. From Server Manager, change the load balancing mode of Team1.
B. Run the New-NetLbfoTeamcmdlet.
C. From Server Manager, add an interface to Team1.
D. Run the Add-NetLbfoTeamMembercmdlet.
Answer: C
GreatExam 70-417 Questions & Answers covers all the knowledge points of the real exam. We update our product frequently so our customer can always have the latest version of the braindumps. We have the most professional expert team to back up our grate quality products. Welcome to try.