Lead2pass Free Microsoft 70-534 Braindumps VCE Updated:
https://www.lead2pass.com/70-534.html
Case Study 1 – VanArsdel, Ltd (Question 1 – Question 8)
Overview
VanArsdel, Ltd. builds skyscrapers, subways, and bridges.
VanArsdel is a leader in using technology to do construction better.

Overview
VanArsdel employees are able to use their own mobile devices for work activities because the company recognizes that this usage enables employee productivity.
Employees also access Software as a Service (SaaS) applications, including DocuSign, Dropbox, and Citrix.
The company continues to evaluate and adopt more SaaS applications for its business. VanArsdel uses Azure Active Directory (AD) to authenticate its employees, as well as Multi-Factor Authentication (MFA). Management enjoys the ease with which MFA can be enabled and disabled for employees who use cloud-based services.
VanArsdel’s on-premises directory contains a single forest.
Helpdesk:
VanArsdel creates a helpdesk group to assist its employees. The company sends email messages to all its employees about the helpdesk group and how to contact it. Configuring employee access for SaaS applications is often a time-consuming task.
It is not always obvious to the helpdesk group which users should be given access to which SaaS applications. The helpdesk group must respond to many phone calls and email messages to solve this problem, which takes up valuable time.
The helpdesk group is unable to meet the needs of VanArsdel’s employees.
However, many employees do not work with the helpdesk group to solve their access problems. Instead, these employees contact their co-workers or managers to find someone who can help them. Also, new employees are not always told to contact the helpdesk group for access problems. Some employees report that they cannot see all the applications in the Access Panel that they have access to. Some employees report that they must re-enter their passwords when they access cloud applications, even though they have already authenticated.
Bring your own device (BYOD):
VanArsdel wants to continue to support users and their mobile and personal devices, but the company is concerned about how to protect corporate assets that are stored on these devices. The company does not have a strategy to ensure that its data is removed from the devices when employees leave the company.
Customer Support
VanArsdel wants a mobile app for customer profile registration and feedback.
The company would like to keep track of all its previous, current, and future customers worldwide. A profile system using third-party authentication is required as well as feedback and support sections for the mobile app.
Migration:
VanArsdel plans to migrate several virtual machine (VM) workloads into Azure.
They also plan to extend their on-premises Active Directory into Azure for mobile app authentication.
Business Requirements
Hybrid Solution:
A single account and credentials for both on-premises and cloud applications Certain applications that are hosted both in Azure and on-site must be accessible to both VanArsdel employees and partners
The service level agreement (SLA) for the solution requires an uptime of 99.9%
The partners all use Hotmail.com email addresses
Mobile App:
VanArsdel requires a mobile app for project managers on construction job sites.
The mobile app has the following requirements:
The app must display partner information.
The app must alert project managers when changes to the partner information occur.
The app must display project information including an image gallery to view pictures of construction projects.
Project managers must be able to access the information remotely and securely.
Security:
VanArsdel must control access to its resources to ensure sensitive services and information are accessible only by authorized users and/or managed devices.
Employees must be able to securely share data, based on corporate policies, with other VanArsdel employees and with partners who are located on construction job sites.
VanArsdel management does NOT want to create and manage user accounts for partners.
Technical Requirements
Architecture:
VanArsdel requires a non-centralized stateless architecture fonts data and services where application, data, and computing power are at the logical extremes of the network.
VanArsdel requires separation of CPU storage and SQL services
Data Storage:
VanArsdel needs a solution to reduce the number of operations on the contractor information table. Currently, data transfer rates are excessive, and queue length for read/write operations affects performance.
A mobile service that is used to access contractor information must have automatically scalable, structured storage
Images must be stored in an automatically scalable, unstructured form.
Mobile Apps:
VanArsdel mobile app must authenticate employees to the company’s Active Directory.
Event-triggered alerts must be pushed to mobile apps by using a custom Node.js script.
The customer support app should use an identity provider that is configured by using the Access Control Service for current profile registration and authentication.
The customer support team will adopt future identity providers that are configured through Access Control Service.
Security:
Active Directory Federated Server (AD FS) will be used to extend AD into Azure.
Helpdesk administrators must have access to only the groups of Azure resources they are responsible for.
Azure administration will be performed by a separate group.
IT administrative overhead must be minimized.
Permissions must be assigned by using Role Based Access Control (RBAC).
Line of business applications must be accessed securely.
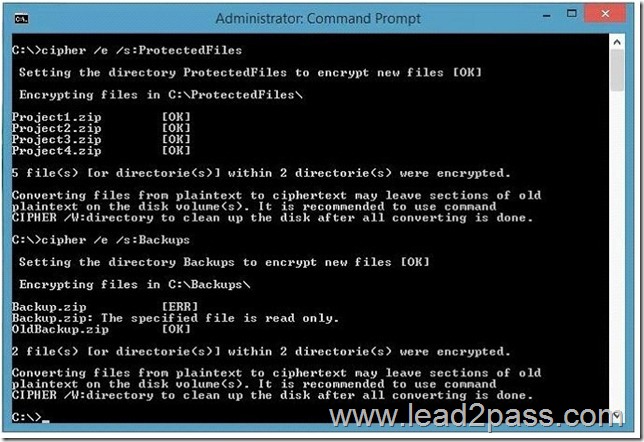
QUESTION 1
You need to assign permissions for the Virtual Machine workloads that you migrate to Azure.
The solution must use the principal of least privileges.
What should you do?
A. Create all VMs in the cloud service named Groupl and then connect to the Azure subscription.
Run the following Windows PowerShell command:
New-AzureRoleAssignment-Mail [email protected]–RoleDefinitionName Contributor-ResoureeGroupName group1
B. In the Azure portal, select an individual virtual machine and add an owner.
C. In the Azure portal, assign read permission to the user at the subscription level.
D. Create each VM in a separate cloud service and then connect to the Azure subscription.
Run the following Windows PowerShell command:
Get-AzureVM | New-AzureRoleAssignment-Mail [email protected] Contributor
Answer: A
Explanation:
* Scenario: Permissions must be assigned by using Role Based Access Control (RBAC).
* Role-Based access control (RBAC) in the Azure Portal and Azure Resource Management API allows you to manage access to your subscription at a fine-grained level. With this feature, you can grant access for Active Directory users, groups, or service principals by assigning some roles to them at a particular scope.
Create a role assignment
Use New-AzureRoleAssignment to create a role assignment.
Example: This will create a role assignment for a group at a resource group level.
PS C:\> New-AzureRoleAssignment -ObjectID <group object ID> -RoleDefinitionName Reader – ResourceGroupName group1
https://azure.microsoft.com/en-gb/documentation/articles/role-based-access-control-powershell/
QUESTION 2
You need to design the system that alerts project managers to data changes in the contractor information app.
Which service should you use?
A. Azure Mobile Service
B. Azure Service Bus Message Queueing
C. Azure Queue Messaging
D. Azure Notification Hub
Answer: C
Explanation:
* Scenario:
/ Mobile Apps: Event-triggered alerts must be pushed to mobile apps by using a custom Node.js script.
/ The service level agreement (SLA) for the solution requires an uptime of 99.9%
* If you are already using Azure Storage Blobs or Tables and you start using queues, you are guaranteed 99.9% availability. If you use Blobs or Tables with Service Bus queues, you will have lower availability.
Note: Microsoft Azure supports two types of queue mechanisms: Azure Queues and Service Bus Queues.
/ Azure Queues, which are part of the Azure storage infrastructure, feature a simple REST- based Get/Put/Peek interface, providing reliable, persistent messaging within and between services.
/ Service Bus queues are part of a broader Azure messaging infrastructure that supports queuing as well as publish/subscribe, Web service remoting, and integration patterns.
https://msdn.microsoft.com/en-us/library/azure/hh767287.aspx
QUESTION 3
You need to recommend a solution that allows partners to authenticate.
Which solution should you recommend?
A. Configure the federation provider to trust social identity providers.
B. Configure the federation provider to use the Azure Access Control service.
C. Create a new directory in Azure Active Directory and create a user account for the partner.
D. Create an account on the VanArsdel domain for the partner and send an email message that contains the password to the partner.
Answer: B
Explanation:
* Scenario: The partners all use Hotmail.com email addresses.
* In Microsoft Azure Active Directory Access Control (also known as Access Control Service or ACS), an identity provider is a service that authenticates user or client identities and issues security tokens that ACS consumes.
The ACS Management Portal provides built-in support for configuring Windows Live ID as an ACS Identity Provider.
Incorrect:
Not C, not D: Scenario: VanArsdel management does NOT want to create and manage user accounts for partners.
https://msdn.microsoft.com/en-us/library/azure/gg185971.aspx
QUESTION 4
You are designing a plan to deploy a new application to Azure.
The solution must provide a single sign-on experience for users.
You need to recommend an authentication type.
Which authentication type should you recommend?
A. SAML credential tokens
B. Azure managed access keys
C. Windows Authentication
D. MS-CHAP
Answer: A
Explanation:
A Microsoft cloud service administrator who wants to provide their Azure Active Directory (AD) users with sign-on validation can use a SAML 2.0 compliant SP-Lite profile based Identity Provider as their preferred Security Token Service (STS) / identity provider. This is useful where the solution implementer already has a user directory and password store on-premises that can be accessed using SAML 2.0. This existing user directory can be used for sign-on to Office 365 and other Azure AD-secured resources.
https://msdn.microsoft.com/en-us/library/azure/dn641269.aspx?f=255&MSPPError=-2147217396
QUESTION 5
You need to prepare the implementation of data storage for the contractor information app.
What should you?
A. Create a storage account and implement multiple data partitions.
B. Create a Cloud Service and a Mobile Service. Implement Entity Group transactions.
C. Create a Cloud Service and a Deployment group. Implement Entity Group transactions.
D. Create a Deployment group and a Mobile Service. Implement multiple data partitions.
Answer: B
Explanation:
* Scenario:
/ VanArsdel needs a solution to reduce the number of operations on the contractor information table. Currently, data transfer rates are excessive, and queue length for read/write operations affects performance.
/ A mobile service that is used to access contractor information must have automatically scalable, structured storage
* The basic unit of deployment and scale in Azure is the Cloud Service.
https://msdn.microsoft.com/en-us/library/azure/dd894038.aspx
QUESTION 6
You need to ensure that users do not need to re-enter their passwords after they authenticate to cloud applications for the first time.
What should you do?
A. Enable Microsoft Account authentication.
B. Set up a virtual private network (VPN) connection between the VanArsdel premises and
Azure datacenter.
Set up a Windows Active Directory domain controller in Azure VM.
Implement Integrated Windows authentication.
C. Deploy ExpressRoute.
D. Configure Azure Active Directory Sync to use single sign-on (SSO).
Answer: D
Explanation:
Single sign-on (SSO) is a property of access control of multiple related, but independent software systems. With this property a user logs in once and gains access to all systems without being prompted to log in again at each of them.
http://en.wikipedia.org/wiki/Single_sign-on
QUESTION 7
Drag and Drop Question
You need to recommend data storage mechanisms for the solution.
What should you recommend? To answer, drag the appropriate data storage mechanism to the correct information type. Each data storage mechanism may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Answer:
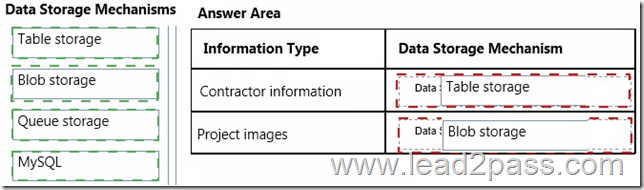
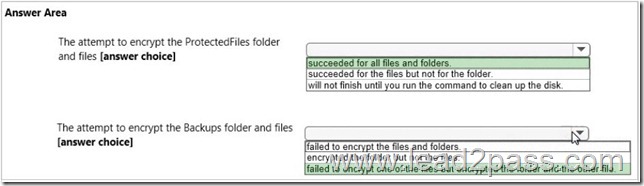
Explanation:
* Use Table storage for Contractor information
* Use Blob for Project Images
* Scenario: VanArsdel needs a solution to reduce the number of operations on the contractor information table. Currently, data transfer rates are excessive, and queue length for read/write operations affects performance.
/ A mobile service that is used to access contractor information must have automatically scalable, structured storage
/ Images must be stored in an automatically scalable, unstructured form.
Note: Blob is an acronym for Binary Large object. Basically Blob is a sequence of bytes – just what an application needs. Blob can hold audio, video, email messages, archived files, zip files or a word processing document in a very general way.
http://www.thewindowsclub.com/understanding-blobqueuetable-storage-windows-azure
QUESTION 8
Hotspot Question
You need to design the contractor information app.
What should you recommend? To answer, select the appropriate options in the answer area.
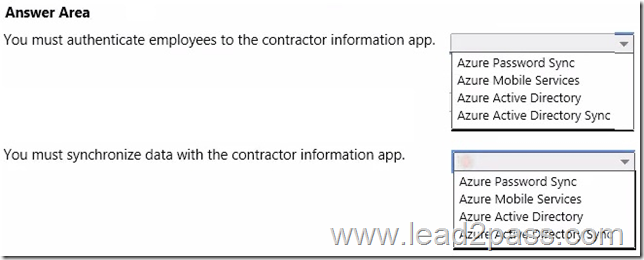
Answer:
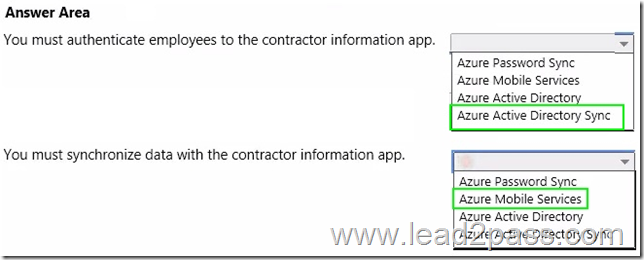
Explanation:
– They also plan to extend their on-premises Active Directory into Azure for mobile app authentication
– VanArsdel mobile app must authenticate employees to the company’s Active Directory.
https://docs.microsoft.com/en-us/azure/app-service-mobile/app-service-mobile-value-prop
QUESTION 9
You are designing an Azure web application.
The solution will be used by multiple customers.
Each customer has different business logic and user interface requirements.
Not all customers use the same version of the .NET runtime.
You need to recommend a deployment strategy.
What should you recommend?
A. Deploy with multiple web role instances.
B. Deploy each application in a separate tenant.
C. Deploy all applications in one tenant.
D. Deploy with multiple worker role instances.
Answer: B
Explanation:
There are two types of tenant environments. The simplest type is a single-tenant application where one customer has 100% dedicated access to an application’s process space. A single Tenant Applications has a separate, logical instance of the application for each customer or client. A single tenant application is much more predictable and stable by its nature since there will never be more than one dedicated customer at any point in time in that VM. That customer has all of its users accessing that dedicated instance of the application.
Multi Tenancy and Windows Azure. Overview of Multi tenant Application and Single tenant Application Architectural considerations.
http://sanganakauthority.blogspot.in/2011/12/multi-tenancy-and-windows-azure.html
QUESTION 10
You design an Azure application that processes images.
The maximum size of an image is 10 MB.
The application includes a web role that allows users to upload images and a worker role with multiple instances that processes the images.
The web role communicates with the worker role by using an Azure Queue service.
You need to recommend an approach for storing images that minimizes storage transactions.
What should you recommend?
A. Store images in Azure Blob service.
Store references to the images in the queue.
B. Store images in the queue.
C. Store images in OneDrive attached to the worker role instances.
Store references to the images in the queue.
D. Store images in local storage on the web role instance.
Store references to the images in the queue.
Answer: A
Explanation:
https://msdn.microsoft.com/en-gb/library/ff803365.aspx
https://msdn.microsoft.com/en-us/library/azure/hh767287.aspx
70-534 dumps full version (PDF&VCE): https://www.lead2pass.com/70-534.html
Large amount of free 70-534 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDaTBTRVp4SktqMXM
You may also need:
70-532 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDbm1XNUxwQUYwaWM
70-533 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDclh4YVRORS1vaHc